
Digital certificates have become part of our lives. We use them for digital signatures, for the encryption of network traffic, when using a web browser for example, for the encryption of e-mails with S/MIME or PGP (Pretty Good Privacy) and for the use of smart cards (bank cards, electronic identity cards, etc.).
But what exactly are digital certificates and how do they work?
Digital certificates are electronic attestations that confirm the authenticity of persons, companies, websites or computers in the digital world. They certify that a public key belongs to a specific entity. They are issued by trustworthy institutions – certificate authorities (CA).
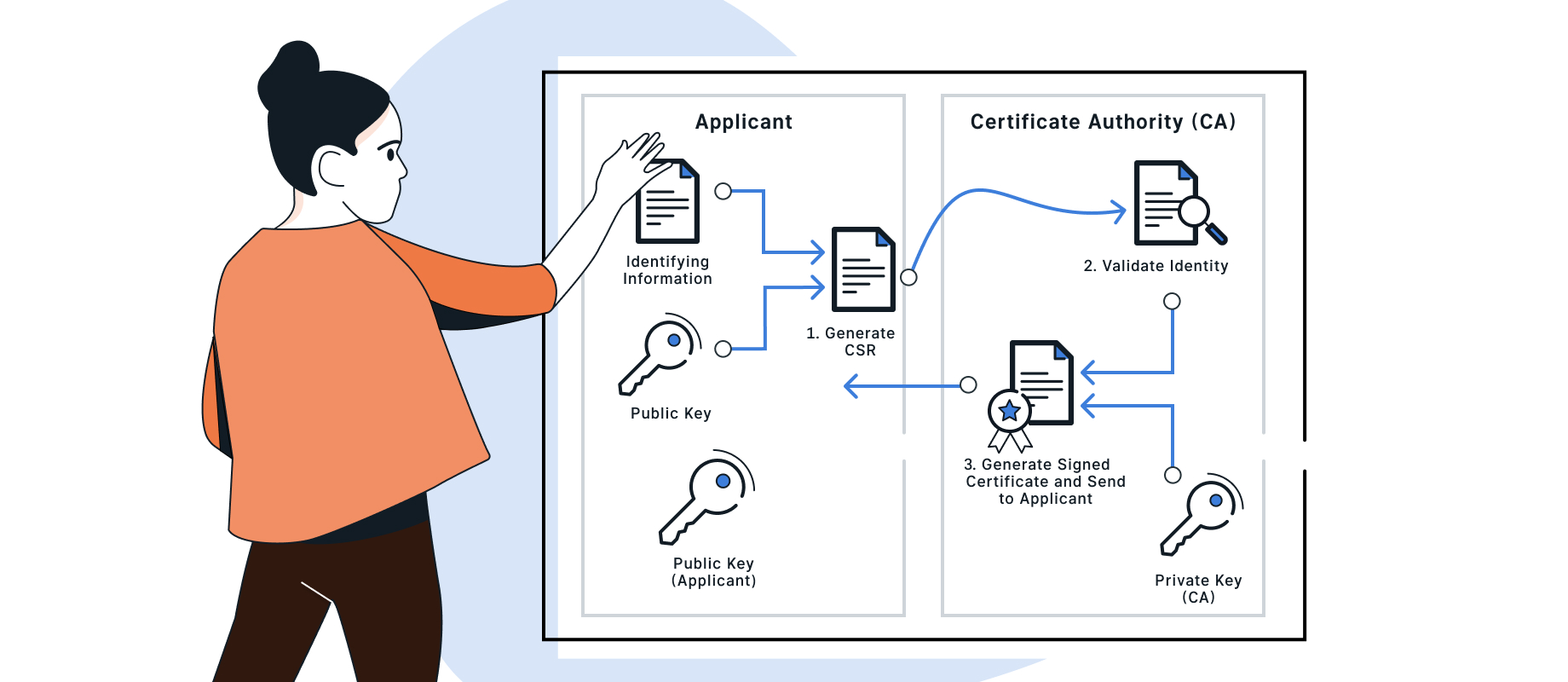
The tasks of a certificate authority (CA) include:
- processing certificate requests: Checking the identity of the applicant, generating, signing and issuing the certificate
- providing their own public key
- maintaining and publishing a list of certificates that are no longer trusted (CRL = Certificate Revocation List)
- operating an OCSP (Online Certificate Status Protocol) Responder Server
Further information and a list of German certification authorities (CA) that are classified as trustworthy by the EU can be found here.
Certificate data
In addition to the name of the owner (individual or other entity), certificates contain other data such as:
- the certificate authority (CA)
- the period of validity (from-to date)
- a serial number
- the public key of the owner
- the certificate authority’s signature
- the purpose
- more data about the owner
If you access a website with a certificate in a web browser (recognisable by the lock to the left of the URL), you can also view all the of the certificate data (e.g. https://itsonix.eu). It is also possible to export the certificate.
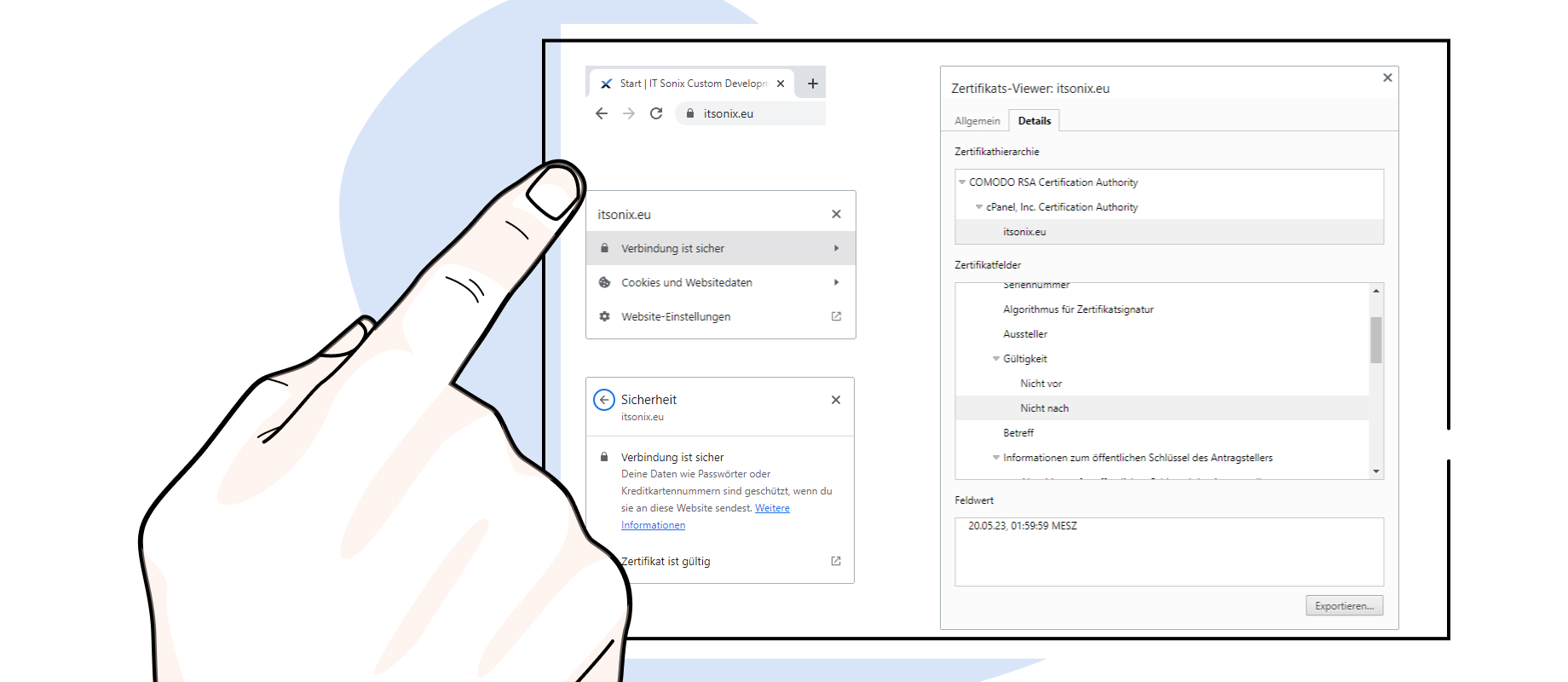
How does certificate verification work for websites?
- A website is requested in the browser
- The server presents its certificate and its public key
- The browser reads the issuer of the certificate and checks its trustworthiness
- The browser internally has a positive list of certification authorities (CA) under "Trusted Root Certification Authorities" and checks the issuer against this list
- If the verification is positive, the certificate is certified as authentic
- The validity of the certificate is checked: The certificate must not have expired or have been eclared invalid by the certification authority before the validity period expires (CRL)
- The address of the web server is checked: Does the address of the web server specified in the certificate match the address entered in the address field of the browser?
- If all these conditions are met, the browser starts to establish an SSL connection with the server
If not all conditions are fulfilled, e.g. because the certificate has expired or comes from an untrustworthy source, you will be informed of this in the browser. However, the certificate can be checked and accepted manually via a dialog. As a general rule, you should not agree to this, and if you do, you should exercise caution and never disclose personal data. It is possible that you have become a victim of a phishing attack. The website you are using may be that of a hacker rather your bank's.
What must be done to get a certificate?
Anyone who needs a certificate (e.g. as the owner of a website) must apply for it via CSR (Certificate Signing Request) at a certification authority (CA). This involves the following steps:
- Generating a key pair (a private key and a public key) – the private key must be protected and must never be leaked publicly
- Creating a CSR file; this is the electronic application form. In addition to the identity of the holder (application data), it also contains their public key
- Taking care of the so-called Proof-of-Possession (PoP) (proof of ownership of the associated private key) – in the form of a self-signature of the application
- Sending the CSR to the registration authority (RA) for verification
- The registration authority (RA) checks the application and passes it on to the certification authority (CA) if the outcome is positive
- The certification authority (CA) issues a new public certificate to the applicant by signing a corresponding X.509 data structure with its private key and sends it to the applicant
What is a certificate chain?
A certificate chain (also certification path) is a sequence of digital certificates. Each certificate is signed with the "higher" certificate.
Certificate chains usually consist of three certificates:
- the actual SSL certificate (short validity period 3 months to 2 years)
- an intermediate certificate (medium period of validity)
- the root certificate (long validity period; usually decades)
Certificate chains are necessary because, on the one hand, it is very time-consuming to exchange trusted root certificates (e.g. in the operating system or in the web browser) and, on the other hand, it must be easy to revoke a certificate or limit its validity.
Root certificates (or the certification authority (CA) that keeps them) are usually specially protected (access protection, multi-eye principle, offline, self-destruction mechanisms). This is so important because if the private key is lost, all SSL certificates based on this root certificate are automatically no longer trustworthy. The exchange of a root certificate and the intermediate certificates takes place within the framework of so-called "key ceremonies" and is subject to strict security rules.
Certificate structure
Over the years, different certificate formats have also developed due to different requirements. The most important among them are:
- X.509: is the best known and most widely used standard for digital certificates and is used, among other things, for:
- secure communication with websites via SSL/TLS
- Encryption of e-mails with S/MIME
- VPN
- ISO 7816: used for Card Verifiable Certificates (CVC), which are applied in smart cards to verify the identity of persons or organisations
- stands for Europay, Mastercard and Visa and is an international standard for chip cards used for payment transactions
X.509 certificate example:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
aa:e3:69:fc:18:ed:ac:80:5c:f7:22:bc:df:c9:1d:a7
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = US, ST = TX, L = Houston, O = "cPanel, Inc.", CN = "cPanel, Inc. Certification Authority"
Validity
Not Before: May 5 00:00:00 2023 GMT
Not After : Aug 3 23:59:59 2023 GMT
Subject: CN = itsonix.eu
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:d9:dc:76:cf:d5:87:af:86:20:ea:44:fb:81:02:
e4:69:3b:27:eb:85:cc:6a:9d:12:c2:48:f5:06:f5:
31:08:93:3b:9d:41:33:99:70:81:91:6c:4c:9e:47:
67:84:c7:dd:fc:fc:31:24:e1:db:8d:be:f5:22:6b:
4d:ca:5b:d4:6a:72:34:b6:22:4c:2e:03:b6:8b:5e:
48:7c:58:9e:9b:59:d4:8e:df:78:58:93:20:19:b9:
56:14:96:23:31:01:48:06:38:3b:22:78:c1:56:ff:
12:51:61:79:9a:6a:3d:e4:96:6b:8a:5f:72:c7:bd:
ac:11:34:2b:6a:3d:64:47:2f:82:83:01:90:2d:f6:
20:4d:e2:7e:0d:97:76:f9:e7:83:17:bf:d1:ad:bf:
b1:72:f6:c8:00:b6:33:59:37:64:e9:e8:41:69:bb:
a4:fd:7b:d4:19:0a:b6:65:a6:18:d5:16:4a:d7:81:
18:23:f2:e3:4f:7d:95:f1:e5:50:49:9b:f4:6d:c2:
f8:ac:8a:5c:4c:6a:75:a1:96:88:b5:0d:e3:17:81:
43:36:56:f4:36:7b:58:56:4d:60:25:db:c2:ed:f2:
bf:4e:bc:2c:36:86:da:ea:4c:98:4b:2e:bb:ad:9f:
c5:be:8c:11:ec:f2:71:20:2b:5b:f3:5b:ad:50:95:
10:c9
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Authority Key Identifier:
7E:03:5A:65:41:6B:A7:7E:0A:E1:B8:9D:08:EA:1D:8E:1D:6A:C7:65
X509v3 Subject Key Identifier:
1B:94:0A:12:DA:21:5D:68:70:54:5D:DA:1E:4F:06:6A:2B:AE:FA:15
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Certificate Policies:
Policy: 1.3.6.1.4.1.6449.1.2.2.52
CPS: https://sectigo.com/CPS
Policy: 2.23.140.1.2.1
X509v3 CRL Distribution Points:
Full Name:
URI:http://crl.comodoca.com/cPanelIncCertificationAuthority.crl
Authority Information Access:
CA Issuers - URI:http://crt.comodoca.com/cPanelIncCertificationAuthority.crt
OCSP - URI:http://ocsp.comodoca.com
CT Precertificate SCTs:
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : AD:F7:BE:FA:7C:FF:10:C8:8B:9D:3D:9C:1E:3E:18:6A:
B4:67:29:5D:CF:B1:0C:24:CA:85:86:34:EB:DC:82:8A
Timestamp : May 5 18:44:13.208 2023 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:46:02:21:00:C8:13:97:C8:F3:8B:B9:F3:F3:3D:F3:
19:2E:75:6C:24:40:37:FD:D5:86:45:AA:AC:59:20:FA:
50:C5:91:96:9B:02:21:00:FD:BD:08:7B:48:26:2E:35:
85:26:0B:04:8C:75:C6:75:6C:12:8B:63:71:52:78:F8:
2B:7B:6D:FB:CC:7F:A7:93
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : 7A:32:8C:54:D8:B7:2D:B6:20:EA:38:E0:52:1E:E9:84:
16:70:32:13:85:4D:3B:D2:2B:C1:3A:57:A3:52:EB:52
Timestamp : May 5 18:44:13.297 2023 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:46:02:21:00:9E:8E:DB:EF:5E:DD:8F:96:E6:41:FE:
9F:0D:57:C0:88:F8:59:5C:72:74:E7:5E:CD:CB:C4:9A:
21:0F:67:FE:94:02:21:00:AF:06:D0:2A:86:D7:34:8F:
92:FF:8E:B1:26:EF:F2:8C:40:57:C5:5D:68:76:2A:72:
83:B4:69:8E:E3:E2:BA:FF
X509v3 Subject Alternative Name:
DNS:itsonix.eu, DNS:www.itsonix.eu
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
0c:db:24:3b:77:fe:7c:3b:51:fd:6d:dc:04:07:b5:26:96:e1:
3b:bd:c2:47:5b:c9:e5:98:c4:58:5d:21:20:20:ba:bc:51:90:
f4:0f:58:5d:e2:d7:ef:7e:5f:9d:89:71:2e:9d:65:b6:93:57:
0a:4b:c7:29:16:cb:22:6e:c7:58:94:d0:b6:9d:45:63:2c:14:
b8:9b:41:97:8e:e9:b3:5f:0c:91:93:26:73:20:04:82:cf:65:
ca:e6:ad:2c:34:2f:76:6f:8f:c9:62:26:2e:f6:4e:59:de:3f:
ce:49:b0:f2:ca:29:b9:a4:4b:bb:d9:aa:cb:e1:94:90:40:1d:
f9:b7:5c:e7:61:d6:1e:44:13:5d:c1:ee:e8:1c:e9:36:bb:19:
24:0e:1e:1d:f8:bd:42:71:50:d8:8a:3d:2e:77:58:91:bd:fc:
f9:7e:d1:4d:de:6d:87:41:76:34:70:a2:a5:ee:a4:81:a4:dc:
77:5b:7e:1c:8b:ce:29:b7:0e:87:c0:9e:7e:1e:af:b1:a2:85:
70:0b:36:93:81:3c:b2:35:6c:f5:ab:2c:ae:78:97:6b:6d:fb:
9e:7c:db:22:07:71:e7:7e:12:e0:94:af:63:3b:6a:c8:14:95:
34:7f:55:7f:13:0b:1e:53:3e:0b:d0:b6:d7:cd:80:d8:97:4e:
38:ba:1b:68Conclusion
Nowadays, digital certificates are the basic prerequisite for ensuring the identity and integrity of data and communication partners in the digital space. Without these certificates, it would be almost impossible to establish trustworthy relationships and exchange sensitive information online. Especially in security-critical areas such as e-banking or e-commerce, digital certificates are indispensable to ensure the security of transactions and information.
Digital certificates also play an important role in many new and emerging technologies and applications (e.g. e-government, smart home, connected car). This also involves the authentication and authorisation of devices and systems. Digital certificates make it possible to establish secure and reliable connections and prevent manipulation and attacks.
Overall, digital certificates are an indispensable part of our digital infrastructure and are likely to become increasingly important as technology changes. Their complexity, different formats and regular updates and renewals will continue to present challenges in the future.
IT Consulting
Learn more about our services